This is an old revision of the document!
Microsoft Azure
This article describes how to establish a Site-To-Site IPSec VPN connection between your Azure server and Privatise network. Please follow the steps below:
Creating a Gateway Subnet
1. In your Azure Management Portal, navigate to the Virtual networks.
2. Select the name of the Virtual Network to which you'd like to create a gateway.
3. Under the Settings section of your VNet page, select Subnets.
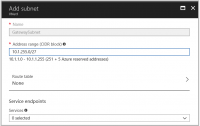
4. Select + Gateway subnet (the name of the subnet is filled in with the value “Gateway subnet” by default).
5. If needed, adjust the auto-filled Address range values to match your configuration requirements.
In case this range is not automatically filled in:
- Go to address space→ +Add
- Select a random /27 bit mask subnet space (for example 10.1.255.0/27)
Creating a Virtual Network Gateway
1. On the left side of the portal page, select + and type Virtual Network Gateway in the Search line.

2. Locate and select the Virtual network gateway.
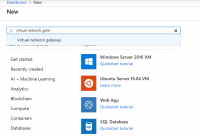
3. Select Create.
4. Fill in the fields with the following information:
Name: Your gateway name.
Region/Location: Select the Virtual Network location\region where your resources are.
Gateway type: Select VPN.
VPN type: Select Route-based.
SKU: Select the gateway SKU from the dropdown. The SKUs listed in the dropdown depend on the VPN you select.
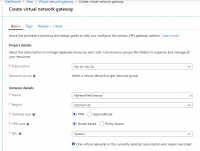
Virtual network:
Select the Virtual network that contains the resources you want to reach via the tunnel.
Select a Virtual network to open the Choose a virtual network page.
If you don't see your VNet, make sure the Location/Region field is pointing to the region in which your virtual network is located.

Gateway subnet address range: You will only see this setting if you did not previously create a gateway subnet for your virtual network. If you previously created a valid gateway subnet, this field will not appear.
Public IP address: This specifies the public IP address object that's associated with the VPN gateway. The public IP address is dynamically assigned to this object when the VPN gateway is created.
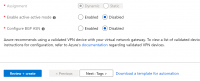
Enable active-active mode: Disabled.
Configure BGP ASN: Disabled.
Select Review+create to begin creating the VPN gateway.
It can take up to 45 minutes for the task to be completed.
Creating a Local Network Gateway
1. In the portal, select + Create a resource.

2. In the search box type “Local network gateway”.
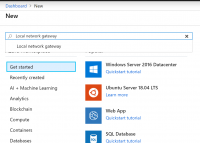
3. Select Local network gateway, then select Create to open the Create local network gateway page.
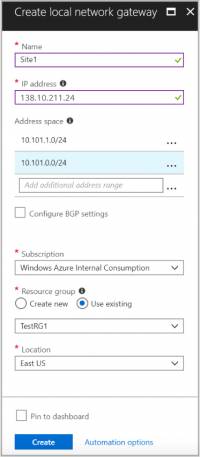
4. Fill in the fields with the following information:
Name Your gateway name.
IP address: This is the public IP address of the VPN device that you want Azure to connect to. Specify your Privatise gateway IP, found next to Static IP under “Roc on Demand” in the Managed Company Portal.
Address Space: Insert your Privatise subnet provided to you by support. (make sure that the ranges you specify here do not overlap with ranges of other networks that you want to connect to).
Subscription: Verify that the correct subscription is showing.
Resource Group: Select the resource group that you want to use. You can either create a new resource group or select one that you have already created.
Location: Select a location that this object will be created in.
You may want to select the location in which your Virtual Network resides, however it is not a requirement.
SKU: Select the gateway SKU from the dropdown. The SKUs listed in the dropdown depend on the VPN you select.
5. Select Create at the bottom of the page to create the local network gateway.
Creating the IPSEC tunnel connection
1. Open your virtual network gateway page.
2. On the sidebar, select All resources.

3. Select the Virtual network gateway you created. Once it opens, go to Settings, select Connections, and then +Add.
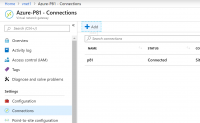
4. Fill in the fields with the following information:
Name Your connection name.
Connection type: Select Site-to-site (IPSec).
Virtual network gateway: Since you are connecting from this gateway this value (the IP you received from Azure) is fixed.
Local network gateway: The local network gateway (your Perimeter 81 network address) which you have just created is the fixed value.
Shared Key: the value here must match the value that you are using for your local on-premises VPN device.
The remaining values for Subscription, Resource Group, and Location are fixed as well.
Select OK to create your connection.
Perimeter 81 Settings
1. Open your Perimeter 81 Management Platform and go to the Network tab.

2. Go to the gateway in your network from which you want to create the tunnel to Azure, select the three-dotted menu (…) beside it, and select Add Tunnel.

3. Select IPSec Site-2-Site Tunnel and select Continue.
4. Fill in the fields with the following information:
Name: Enter a name of your choice.
Shared Secret: Enter the same Shared secret you set in the Azure Portal.
Public IP: Enter the Azure Virtual network gateway public IP.
Remote ID: Enter the Azure Virtual network gateway remote ID.
Perimeter 81 Gateway Proposal Subnets: Choose the purposed IP range.
Remote Gateway Proposal Subnets: Enter the Azure Virtual network gateway subnet/range.
Advanced Settings
IKE Version: V2
IKE Lifetime: 1h
Tunnel Lifetime: 1h
Dead Peer Detection Delay: 10s
Dead Peer Detection Timeout: 30s
Encryption (Phase 1) : aes256
Encryption (Phase 2) : aes256
Integrity (Phase 1) : sha1
Integrity (Phase 2): sha1
Diffie-Hellman Groups (Phase 1): 2
Deffie-Hellman Groups (Phase 1): 2

5. Select Add Tunnel.
Verifying the VPN connection
1. Go to the Azure Portal and select All Resources.
2. Select the Virtual network gateway.
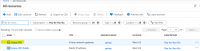
3. Go to Connections.
4. Select the connection you created.
5. Under the Overview tab, make sure that the Status is Connected.