Using Privatise for Remote Access
Secure Remote access using Privatise is easy to deploy, and can replace clunky hardware. It can be used for encrypted RDP, file sharing, and integration with a Windows server DC for connecting remotely to an Active Directory domain.
The advantage over using a Privatise Server Agent is that it's easy to setup & allows for secure remote access without having to expose an entire LAN. This makes the connection more secure.
1. You can use Privatise to connect remotely via the Privatise VLAN while still allowing your internal office machines to connect over the normal LAN.
2. Privatise supports Windows Server 2012 and above for integration with your Active Directory Domain Controller.
3. You can create custom Fully Qualified Domain Names and attach them to static internal IPs (NAT'S) of the Privatise agents.
Remote Access is supported by version 2.0.3 on the Windows Agent and above.
Important: When joining an AD Domain, make sure that you have admin access to that client PC in case of any issues or if you have to reset the domain!
Adding a Domain Controller Agent
To connect to a Windows Server 2012 and above, you will have to fill the following steps.
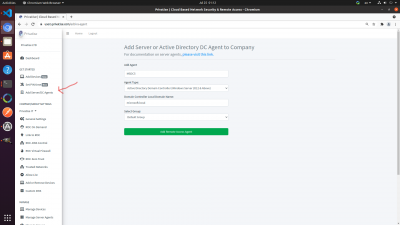
1. Click on Add Server or Active Directory DC Agent.
2. You will be brought to a page to add either an Active Directory DC Agent or File Sharing Server Agent.
3. Add a name for the Domain Controller agent. This is for your own records and keeping things organised.
4. Choose Active Directory Domain Controller.
5. Add the local domain of your DC. For example:: ford.local. Please make sure that the local domain of your DC is NOT accessible over the public internet.
You should then make sure to add the DC domain to your DNS-Dashboard local records. To do that:
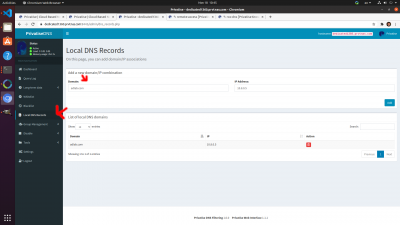
Go to your ROC-DNS Control Dashboard.
1. Go to Local DNS Records
2. Add a Fully Qualified Domain Name (FQDN) of your Domain Controller on the left, and static IP of the Privatise agent you want to connect to.
Configuring the Domain Controller
Please make sure to have the following settings configured after installing Privatise on your Domain Controller (Installation Steps are below):
1. Go to network adapters → TAP Adapter V9 → Right Click Properties → IPV4 → Right Click Properties → Advanced → Unclick “Register This Connection for DNS”.
2. Go to DNS Manager → Domain Controller → Server → Right Click Properties → Interfaces → Click on “Listen on All Addresses”.
Installation
To install the Server Agent, you should login to the server you want to install it on:
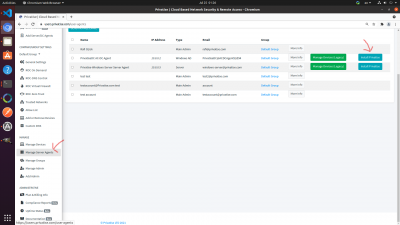
1. Then login to your managed company portal from the server itself.
2. Go to “Manage Server Agents” and Install Privatise with the corresponding agent directly onto the server as seen in the image below.
3. Install the downloaded Privatise Installer executable on the server. After this, follow the steps above in “configuring Domain Controller”.
Troubleshooting
Q. Can't Connect to AD Domain Controller
A. Check IPConfig on the AD DC, and make sure that it has the correct Static IP. Make sure that you only used the agent once, as static IPs do not support multiple installs. On the client machine, make sure that the agent you have installed is in the same Privatise group as the AD DC in the Company Dashboard.
Q. I'm not able to add an AD DC or File Sharing Agent
A. Make sure that the group you want to add the agent to has a ROC. Please see Provisioning a ROC for more information.
Q. Installing an agent broke my file sharing server or DC locally & I had to remove it. What happened?
A. Most likely you did not install the correct agent on the DC or file sharing server. DC & file sharing agents are specifically configured to allow for normal LAN access.
Q. Privatise keeps restarting on the Domain Controller
A. Disable DHCP autoconfiguration. Please see Disabling DHCP Autoconfiguration for more information.
Q: I can't connect to the DC remotely over Privatise A. When you first join, you should use the FQDN and include the .local in it. for example ford.local. When prompted for the username and password, the username should be DOMAIN\User. For example Ford\Tom.