ROC Virtual Firewall
By default, the ROC virtual firewall is locked down again most inbound traffic. Internal traffic between Privatise agents is allowed and can be controlled with ROC ZTNA or Zero Trust.
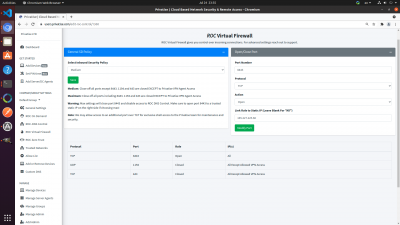
The ROC Virtual Firewall looks like this:
There are a few ports that have to be open for Privatise to work, and ports that can be controlled:
1. Ports 1194 (UDP) and 443 (TCP) must be open as they are used for Privatise agents to connect. They are only accessible via secure certificates.
2. 8443 is open for the DNS-Dashboard. You can close it completely by setting the Inbound Security Policy to Maximum, or link it to a specific static IP in the open/close port on the right. We recommend opening the DNS-Dashboard only to certain IPs.